1 views
実現する機能
Let’s Encrypt は、無料で利用できる自動化されていてオープンな認証局(CA)です。インターネット上での身分証明書にあたるssl証明書は、高額で手が出ませんが、時代は確実にssl証明書無しではサイトにすら来てもらえない厳しい時代に突入していることは確かです。
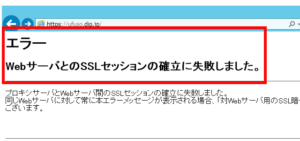
それを目の当たりにできるのが職場です。インターネットを自由に閲覧できる職場でも、自己作成したssl証明書では閲覧できないようになってきています。私の職場でも同じ状況です。職場から自宅サーバーにアクセスすると、下図の画面が表示されて閲覧できませんでした。
そこで、今回は自作ではなく、外部認証局が発行してくれる無料のssl証明書を取得して、その効果を検証してみました。以下は、その取得までを綴った備忘録です。
自宅サーバーにssl証明書取得に必要なソフトをDownload&Install
以下の黒背景部分はGNOME端末を表示しています。紫色はキーボードから入力するコマンド(コピペした方が楽ですが、コマンドは覚えられません)、緑はコマンドや処理内容の説明、白は自動表示する部分、赤は注意書きです。「tu」部分はあなたのUser名に置き換えてください。
#ssl証明書作成にepel-releaseが必要 [root@ufuso ~]# yum install epel-release #ssl証明書作成に必要なソフトのDownload。apache使用者は、 「certbot certbot-nginx」部分を「python-certbot-apache」に変更のこと [root@ufuso ~]# yum --enablerepo=epel -y install certbot certbot-nginx インストール: certbot.noarch 0:0.19.0-1.el7 python2-certbot-nginx.noarch 0:0.19.0-1.el7 依存性関連をインストールしました: dialog.x86_64 0:1.2-4.20130523.el7 pyOpenSSL.x86_64 0:0.13.1-3.el7 pyparsing.noarch 0:1.5.6-9.el7 python-backports.x86_64 0:1.0-8.el7 python-backports-ssl_match_hostname.noarch 0:3.4.0.2-4.el7 python-cffi.x86_64 0:1.6.0-5.el7 python-chardet.noarch 0:2.2.1-1.el7_1 python-enum34.noarch 0:1.0.4-1.el7 python-idna.noarch 0:2.4-1.el7 python-ipaddress.noarch 0:1.0.16-2.el7 python-ndg_httpsclient.noarch 0:0.3.2-1.el7 python-parsedatetime.noarch 0:1.5-3.el7 python-ply.noarch 0:3.4-11.el7 python-pycparser.noarch 0:2.14-1.el7 python-requests.noarch 0:2.6.0-1.el7_1 python-setuptools.noarch 0:0.9.8-7.el7 python-six.noarch 0:1.9.0-2.el7 python-urllib3.noarch 0:1.10.2-3.el7 python-zope-component.noarch 1:4.1.0-3.el7 python-zope-event.noarch 0:4.0.3-2.el7 python-zope-interface.x86_64 0:4.0.5-4.el7 python2-acme.noarch 0:0.19.0-1.el7 python2-certbot.noarch 0:0.19.0-1.el7 python2-configargparse.noarch 0:0.11.0-1.el7 python2-cryptography.x86_64 0:1.7.2-1.el7_4.1 python2-dialog.noarch 0:3.3.0-6.el7 python2-future.noarch 0:0.16.0-2.el7 python2-mock.noarch 0:1.0.1-9.el7 python2-psutil.x86_64 0:2.2.1-2.el7 python2-pyasn1.noarch 0:0.1.9-7.el7 python2-pyrfc3339.noarch 0:1.0-2.el7 pytz.noarch 0:2016.10-2.el7 完了しました! |
自宅サーバー全ドメインのssl証明書を取得
#ssl証明書の取得。「--nginx」=我が家のウェブサーバー、Apacheなら 「--apache」。「-d」の後に自宅サーバーのdomain名を入力。設定例は nginxに2個登録している我が家の場合で説明しています。 [root@ufuso ~]# certbot run --nginx -d ufuso.dip.jp -d topi.0t0.jp Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator nginx, Installer nginx #emailを登録してエンターキー押下(障害時のサポートに必要) Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): tu@ufuso.dip.jp Starting new HTTPS connection (1): acme-v01.api.letsencrypt.org ------------------------------------------------------------------------------- Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must agree in order to register with the ACME server at https://acme-v01.api.letsencrypt.org/directory ------------------------------------------------------------------------------- #「A」入力後リターンキー押下。同意しないと先に進めない (A)gree/(C)ancel: A ------------------------------------------------------------------------------- Would you be willing to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about EFF and our work to encrypt the web, protect its users and defend digital rights. ------------------------------------------------------------------------------- #「N」入力後リターンキー押下。あなたのemailを利用してもいいかの質問なので (Y)es/(N)o: N Obtaining a new certificate Performing the following challenges: tls-sni-01 challenge for ufuso.dip.jp tls-sni-01 challenge for topi.0t0.jp Waiting for verification... Cleaning up challenges #ドメイン「dip.jp」は登録が多いので登録制限中とのこと An unexpected error occurred: There were too many requests of a given type :: Error creating new cert :: too many certificates already issued for: dip.jp Please see the logfiles in /var/log/letsencrypt for more details. IMPORTANT NOTES: - Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal. |
ssl証明書を個別編集
#「topi.0t0.jp」のssl証明書を個別に設定 [root@ufuso ~]# certbot Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator nginx, Installer nginx Starting new HTTPS connection (1): acme-v01.api.letsencrypt.org #「topi.0t0.jp」なので、「1」を入力してエンターキー押下 Which names would you like to activate HTTPS for? ------------------------------------------------------------------------------- 1: topi.0t0.jp 2: ufuso.dip.jp 3: ufuso.org ------------------------------------------------------------------------------- Select the appropriate numbers separated by commas and/or spaces, or leave input blank to select all options shown (Enter 'c' to cancel): 1 Obtaining a new certificate Performing the following challenges: tls-sni-01 challenge for topi.0t0.jp Waiting for verification... Cleaning up challenges Deployed Certificate to VirtualHost /etc/nginx/nginx.conf for set(['topi.0t0.jp']) #常にHTTPSでの接続をするなら「2」を入力してエンターキー押下。それ以外は「1」 Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access. ------------------------------------------------------------------------------- 1: No redirect - Make no further changes to the webserver configuration. 2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for new sites, or if you're confident your site works on HTTPS. You can undo this change by editing your web server's configuration. ------------------------------------------------------------------------------- Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2 Redirecting all traffic on port 80 to ssl in /etc/nginx/nginx.conf ------------------------------------------------------------------------------- Congratulations! You have successfully enabled https://topi.0t0.jp You should test your configuration at: https://www.ssllabs.com/ssltest/analyze.html?d=topi.0t0.jp ------------------------------------------------------------------------------- IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/topi.0t0.jp/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/topi.0t0.jp/privkey.pem Your cert will expire on 2018-02-19. To obtain a new or tweaked version of this certificate in the future, simply run certbot again with the "certonly" option. To non-interactively renew *all* of your certificates, run "certbot renew" - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le |
自宅サーバーから別PCに転送しているドメインのssl証明書を編集
#「ufuso.org」のssl証明書を個別に設定 [root@ufuso ~]# certbot Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator nginx, Installer nginx Starting new HTTPS connection (1): acme-v01.api.letsencrypt.org #「ufuso.org」なので、「3」を入力してエンターキー押下 Which names would you like to activate HTTPS for? ------------------------------------------------------------------------------- 1: topi.0t0.jp 2: ufuso.dip.jp 3: ufuso.org ------------------------------------------------------------------------------- Select the appropriate numbers separated by commas and/or spaces, or leave input blank to select all options shown (Enter 'c' to cancel): 3 Cert not yet due for renewal You have an existing certificate that has exactly the same domains or certificate name you requested and isn't close to expiry. (ref: /etc/letsencrypt/renewal/ufuso.org.conf) What would you like to do? #期間延長なら「2」を入力してエンターキー押下。再Installは「1」 ------------------------------------------------------------------------------- 1: Attempt to reinstall this existing certificate 2: Renew & replace the cert (limit ~5 per 7 days) ------------------------------------------------------------------------------- Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2 Renewing an existing certificate Performing the following challenges: tls-sni-01 challenge for ufuso.org Waiting for verification... Cleaning up challenges Deployed Certificate to VirtualHost /etc/nginx/nginx.conf for set(['ufuso.org']) #常にHTTPSでの接続をするなら「2」を入力してエンターキー押下。それ以外は「1」 Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access. ------------------------------------------------------------------------------- 1: No redirect - Make no further changes to the webserver configuration. 2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for new sites, or if you're confident your site works on HTTPS. You can undo this change by editing your web server's configuration. ------------------------------------------------------------------------------- Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2 The appropriate server block is already redirecting traffic. To enable redirect anyway, uncomment the redirect lines in /etc/nginx/nginx.conf. ------------------------------------------------------------------------------- Your existing certificate has been successfully renewed, and the new certificate has been installed. The new certificate covers the following domains: https://ufuso.org You should test your configuration at: https://www.ssllabs.com/ssltest/analyze.html?d=ufuso.org ------------------------------------------------------------------------------- IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/ufuso.org/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/ufuso.org/privkey.pem Your cert will expire on 2018-02-22. To obtain a new or tweaked version of this certificate in the future, simply run certbot again with the "certonly" option. To non-interactively renew *all* of your certificates, run "certbot renew" - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le |
ssl証明書の取得でnginxの設定が自動変更されたようなので内容を確認
#nginxの設定ファイルを開く。朱書きが自動追記部分 [root@ufuso ~]# vi /etc/nginx/nginx.conf #user nginx; user apache; #worker_processes 1; worker_processes auto; error_log /var/log/nginx/error.log warn; pid /var/run/nginx.pid; events { worker_connections 1024; use epoll; #I/O多重化指定 } http { include /etc/nginx/mime.types; default_type application/octet-stream; log_format main '$remote_addr - $remote_user [$time_local] "$request" ' '$status $body_bytes_sent "$http_referer" ' '"$http_user_agent" "$http_x_forwarded_for"'; access_log /var/log/nginx/access.log main; sendfile on; #tcp_nopush on; keepalive_timeout 65; gzip on; include /etc/nginx/conf.d/*.conf; server { listen 80 ; listen [::]:80; #通信の暗号化(ssl)。rainloopはhttps://接続なので必要 listen 443 ssl http2; #Webサーバーの指定 server_name topi.0t0.jp; #Webフォルダの指定 #root /var/www/html; root /usr/share/nginx/html; index index.php index.html index.htm; #暗号化方式の指定 ssl_protocols TLSv1 TLSv1.1 TLSv1.2; #サーバのSSL暗号設定をクライアントのそれより優先 ssl_prefer_server_ciphers on; #暗号技術の組み合わせを指定 ssl_ciphers ECDHE+RSAGCM:ECDH+AESGCM:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:!aNULL!eNull:!EXPORT:!DES:!3DES:!MD5:!DSS; #自己証明書の場所を入力(事例はmod-sslの場合) ssl_certificate /etc/letsencrypt/live/topi.0t0.jp/fullchain.pem; # managed by Certbot #秘密鍵の場所を入力(事例はmod-sslの場合) ssl_certificate_key /etc/letsencrypt/live/topi.0t0.jp/privkey.pem; # managed by Certbot if ($scheme != "https") { return 301 https://$host$request_uri; } # managed by Certbot } server { listen 80 default_server; listen [::]:80 default_server; #通信の暗号化(ssl)。rainloopはhttps://接続なので必要 listen 443 ssl http2; #Webサーバーの指定 server_name ufuso.dip.jp; #Webフォルダの指定 root /var/www/html; #root /usr/share/nginx/html; index index.php index.html index.htm; #暗号化方式の指定 ssl_protocols TLSv1 TLSv1.1 TLSv1.2; #サーバのSSL暗号設定をクライアントのそれより優先 ssl_prefer_server_ciphers on; #暗号技術の組み合わせを指定 ssl_ciphers ECDHE+RSAGCM:ECDH+AESGCM:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:!aNULL!eNull:!EXPORT:!DES:!3DES:!MD5:!DSS; #自己証明書の場所を入力(事例はmod-sslの場合) ssl_certificate /etc/pki/tls/certs/server.crt; #秘密鍵の場所を入力(事例はmod-sslの場合) ssl_certificate_key /etc/pki/tls/certs/server.key; if ($scheme != "https") { return 301 https://$host$request_uri; } # managed by Certbot # Load configuration files for the default server block. include /etc/nginx/default.d/*.conf; #phpを使うための設定。fastcgi経由なのでその設定がメイン location ~ \.php$ { include /etc/nginx/fastcgi_params; fastcgi_pass 127.0.0.1:9000; fastcgi_index index.php; fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name; } error_page 404 /404.html; location = /40x.html { } error_page 500 502 503 504 /50x.html; location = /50x.html { } } server { server_name ufuso.org; #クライアントがアクセスするURL proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header Host $http_host; location / { proxy_pass http://192.168.24.240; #ウェブサーバーBのIPアドレス } if ($scheme != "https") { return 301 https://$host$request_uri; } # managed by Certbot # Redirect non-https traffic to https # if ($scheme != "https") { # return 301 https://$host$request_uri; # } # managed by Certbot } server { listen 443 ssl http2; server_name ufuso.org; #クライアントがアクセスするURL proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header Host $http_host; location / { proxy_pass https://192.168.24.240; #ウェブサーバーBのIPアドレス } ssl_certificate /etc/letsencrypt/live/ufuso.org/fullchain.pem; # managed by Certbot ssl_certificate_key /etc/letsencrypt/live/ufuso.org/privkey.pem; # managed by Certbot } } |
職場から自宅サーバーにアクセスできたので、一定の公証力はあるようです
ssl証明書自動更新の設定(crontab)
#自動更新コマンドの実行(更新時期30日未満になると更新) [root@ufuso ~]# certbot renew --pre-hook "service nginx stop" --post-hook "service nginx start" Saving debug log to /var/log/letsencrypt/letsencrypt.log ------------------------------------------------------------------------------- Processing /etc/letsencrypt/renewal/topi.0t0.jp.conf ------------------------------------------------------------------------------- Cert not yet due for renewal ------------------------------------------------------------------------------- Processing /etc/letsencrypt/renewal/ufuso.org.conf ------------------------------------------------------------------------------- Cert not yet due for renewal #更新時期30日未満ではないので更新しないが、結果は成功 ------------------------------------------------------------------------------- The following certs are not due for renewal yet: /etc/letsencrypt/live/topi.0t0.jp/fullchain.pem (skipped) /etc/letsencrypt/live/ufuso.org/fullchain.pem (skipped) No renewals were attempted. No hooks were run. ------------------------------------------------------------------------------- #crontabをインストール [root@ufuso ~]# yum -y install cronie-noanacron インストール: cronie-noanacron-1.4.11-17.el7.x86_64 完了しました! #crontabに設定を追加する。 [root@ufuso~]# vi /etc/crontab SHELL=/bin/bash PATH=/sbin:/bin:/usr/sbin:/usr/bin MAILTO=root # For details see man 4 crontabs # Example of job definition: # .---------------- minute (0 - 59) # | .------------- hour (0 - 23) # | | .---------- day of month (1 - 31) # | | | .------- month (1 - 12) OR jan,feb,mar,apr ... # | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat # | | | | | # * * * * * user-name command to be executed #毎週日曜の午前5時に更新するように設定。「-q」でログ出力を省略。 apacheを使用なら「nginx」を「httpd」に変更 0 5 * * 0 root certbot renew -q --pre-hook "service nginx stop" --post-hook "service nginx start" |
以上
コメントを残す